How To Protect RDP From Brute-Force Attacks?
How to secure your remote desktop? The expansion of remote communication protocols has provided an opportunity for cybercriminals to further develop ransomware attacks.
They predicted that most companies and organizations do not have enough time and resources to implement a secure Remote Desktop Protocol (RDP) and through this vulnerability, they can easily execute their attacks.
Many attacks can happen on your remote desktop service. Brute-force is one of the most common attacks to access remote desktop login details. As a result, hackers use this method to check all ways to enter the server.
But as you know, prevention is better than cure. As a result, it is better to block the IP that tries to access your remote desktop again and again. How exactly should you do this? be with us.
Secure your RDP: Buy Windows VPS today for fortified protection against brute-force attacks.
How do cybercriminals implement their malware attacks using Remote Desktop Protocol (RDP)?
Remote Desktop is usually considered a safe and secure tool on a private network. However, if access to the RDP port is open from other insecure networks (such as the Internet), it may cause serious problems. Because it allows anyone to remotely connect to the server.
If this process is successful, the hacker can gain access to the server and apply the desired changes on the server based on the user’s access level.
Stop Brute-Force Attacks on Remote Desktop with RDP Guard

In this section, we examine how to block suspicious IPs through the RDPGuard software.
Using Windows firewall and system event log, it detects suspicious IPs and immediately blocks them. Also, you can only protect your desired ports.
In addition to remote desktop, this program also protects many other services.
Protection services against Bruteforce attacks
RDP
FTP
IMAP
POP3
MySQL
MS-SQL
VoIP/SIP
WebForms
RD Web Access
Steps to Protect Your Remote Desktop in Brute-Force Using RdpGuard
Download RdpGuard.
Start and complete the installation process.
Run the software and check which service you want to protect.

Step 1: Download RdpGuard from its website.
Second step: Install RdpGuard in Windows VPS.
1. After running the downloaded file, select Next to start the process.
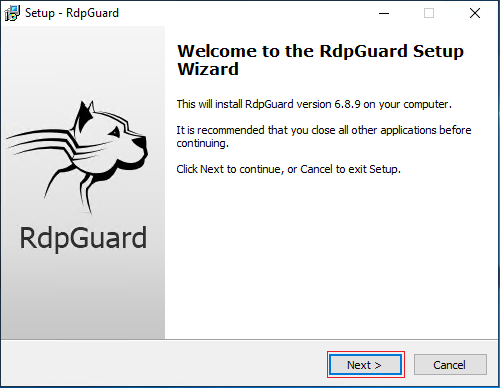
2. Check “I accept the agreement” and select Next.
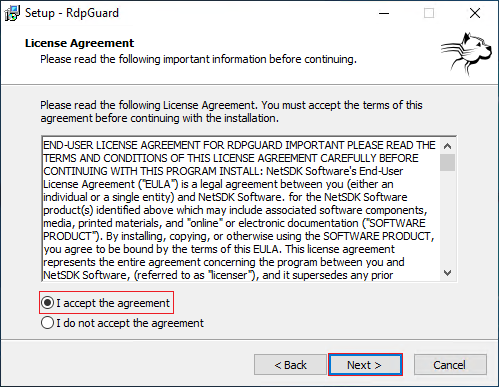
3. Select the desired location to download. Or select the default address and select Next.
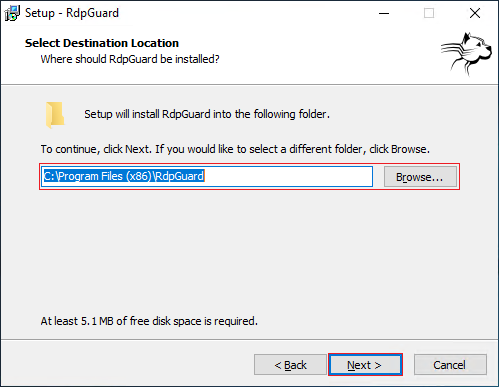
4. In the next section, you will be asked whether you want the desktop icon to be created and whether you want it for the current user only or for all users.
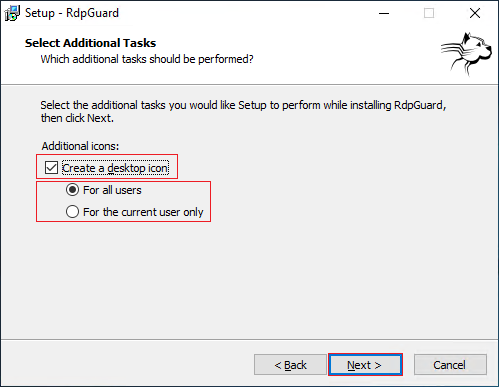
5. congratulations! The installation is finished. Now check the “Start RdpGuard now” option and select Finish.
Third step: RdpGuard configurations and settings
When the software opens, you will see that Remote Desktop Service protection is enabled by default. As a result, you don’t need to make any changes to this. And as you can see, it blocked some IPs a few minutes after installation.
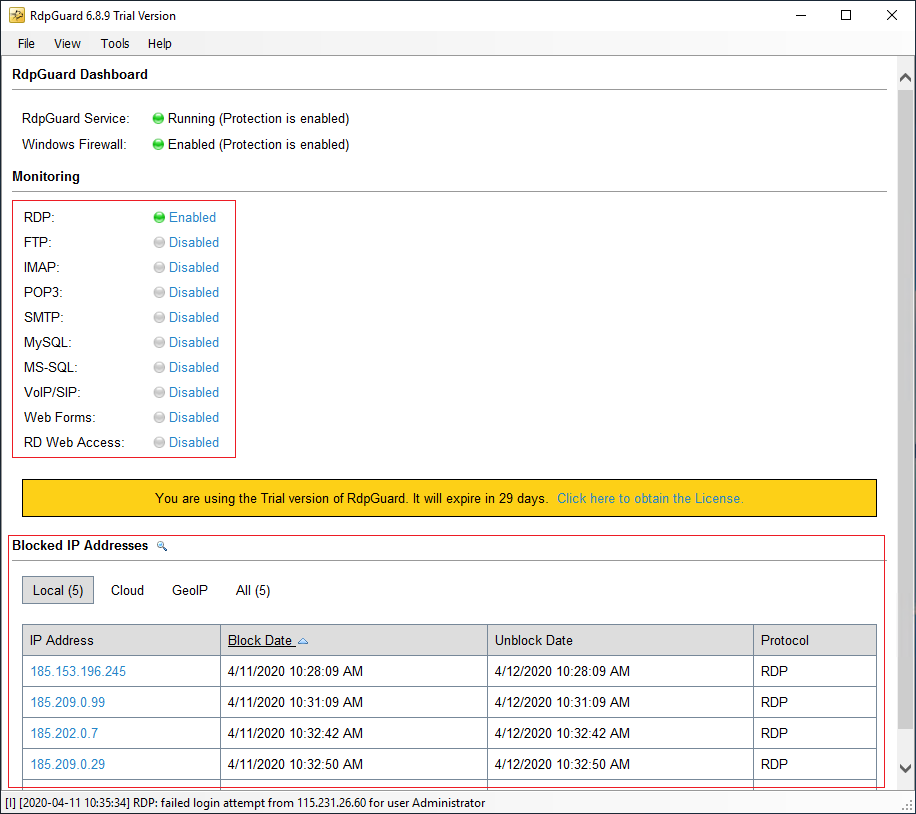
And if you want to enable the protection of another service, you can easily select “Disable” next to each service to enable it. For example, now we enable FTP service protection.
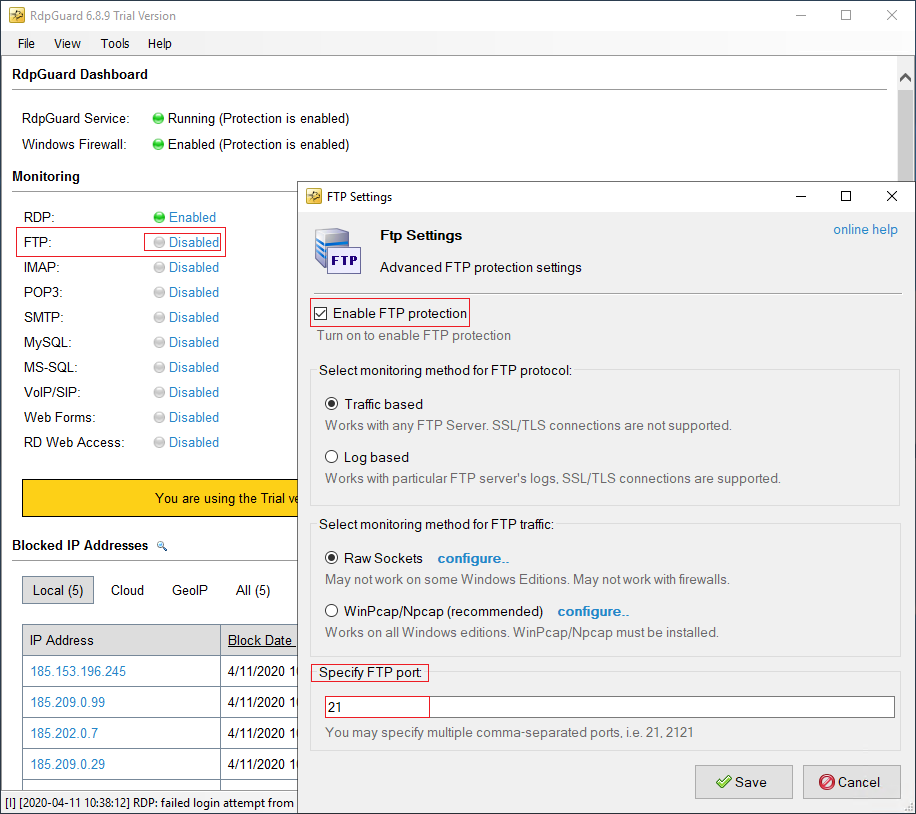
To enable protection on the new page, you can select “Enable FTP Protection” and configure the settings mentioned. You can enable the protection of other services.
Note: After buying a remote desktop, if you don’t pay attention to some things, your server may be easily hacked, and one of these things was brute-force, which we talked about how to stop.
Final point :
The ever-increasing expansion of remote jobs and the increased use of remote desktop services have made cybercriminals take full advantage of this opportunity and implement their malware attacks in this way. Taking a proactive approach to securing this service allows organizations to take full advantage of the potential of working remotely and minimize the risk of remote desktop (RDP) malware attacks.







